
CIRCE
A tool that uses cyber-psychological tactics to
exploit human vulnerabilities in cyber attackers
OUR CORE R&D / These systems range from individual
autonomous robotic platforms to large-scale, multi-agent systems
for information management, command & control
These systems range from individual autonomous robotic platforms to large-scale, multi-agent systems for information management, command & control

A tool that uses cyber-psychological tactics to
exploit human vulnerabilities in cyber attackers

An automated cybertraining tool that customizes behavior to meet training objectives
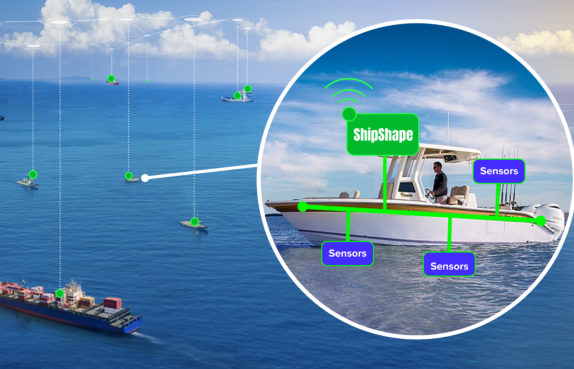
Boat safety challenges and real-time performance using onboard sensor data
Cyber meta-monitor technology to mitigate in-flight attacks

A forensic analysis tool for cybertechnical and cybersocial attacks

Automatically verify code, catch errors, and seamlessly make recommendations

A cyber-attack detection and inference device
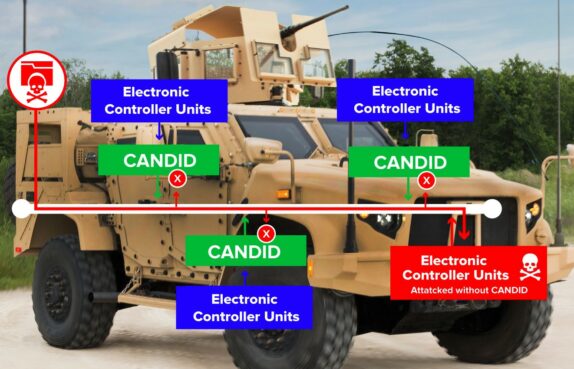
A system that detects and prevents cybersecurity breaches in military ground vehicles

Cyber adversary modeling and simulation

A secure neural network that protects sensitive information

Probabilistic representation of intent commitments to ensure software survival

War gaming exercises without need for extensive adversary behavior modeling experience

Predictive malware defense research