
Strengthens cyber resilience for your business
Strengthens cyber resilience for your business
Automated risk assessments
and mitigation plans
Identifying potential vulnerabilities in your ecosystem is a critical first step in understanding the risks that directly affect your business. Odineye’s security assessment mitigates against those threats to protect what matters most.
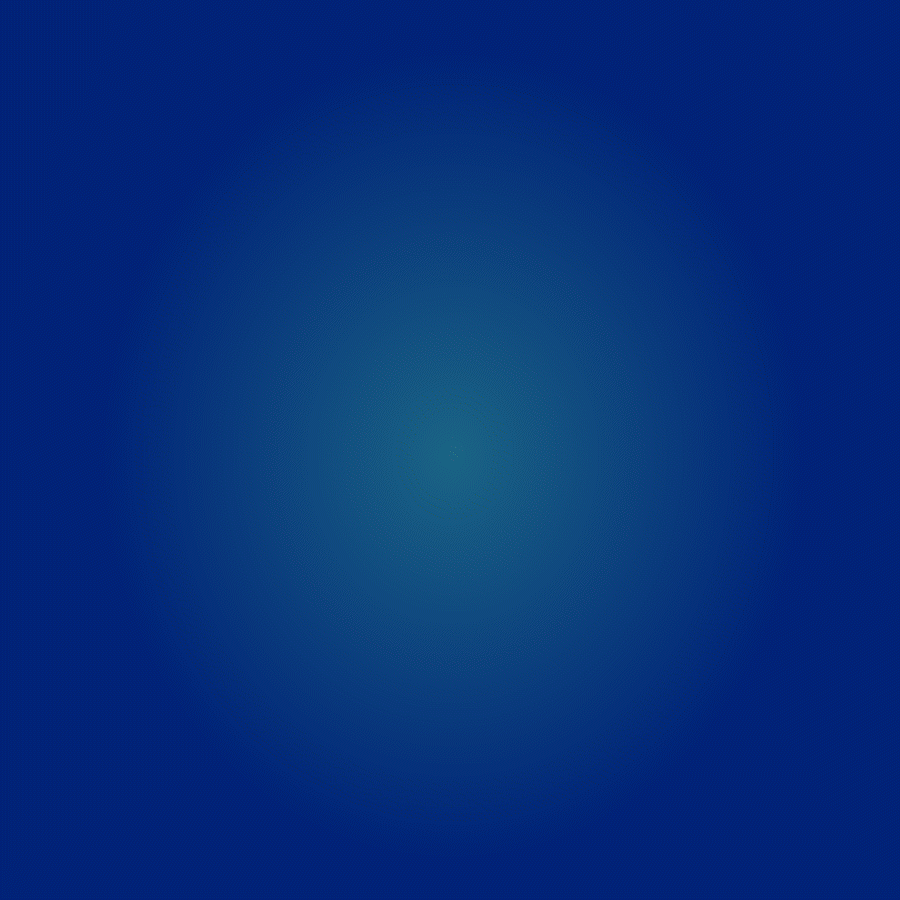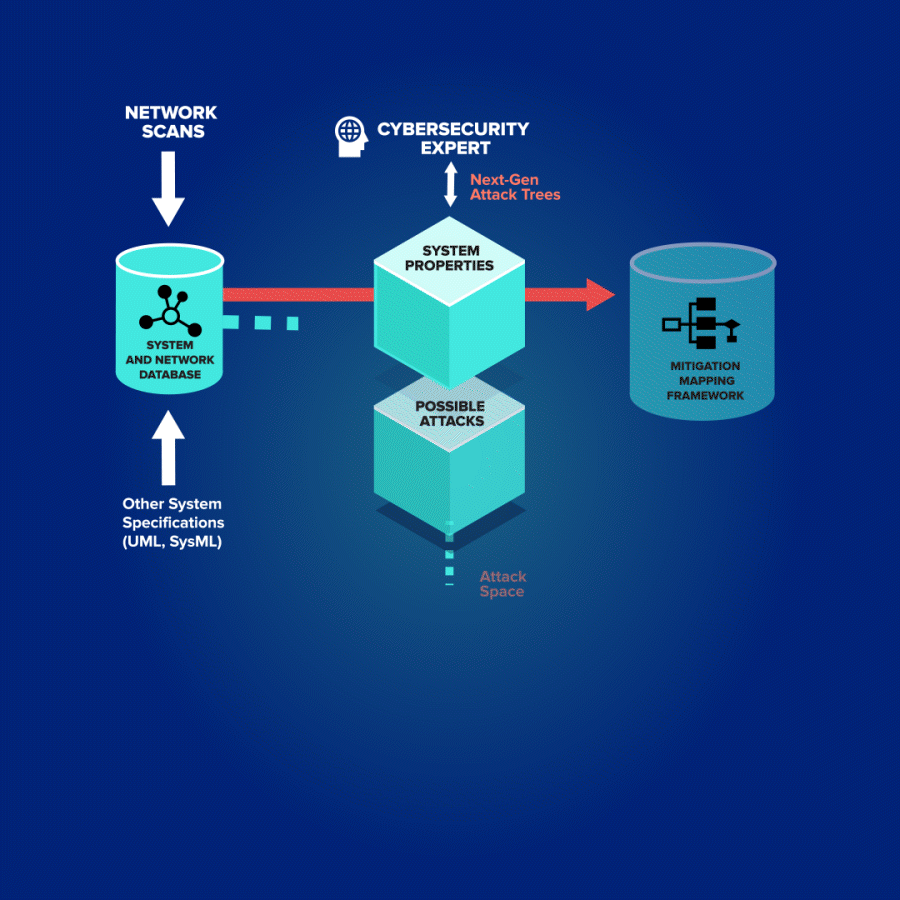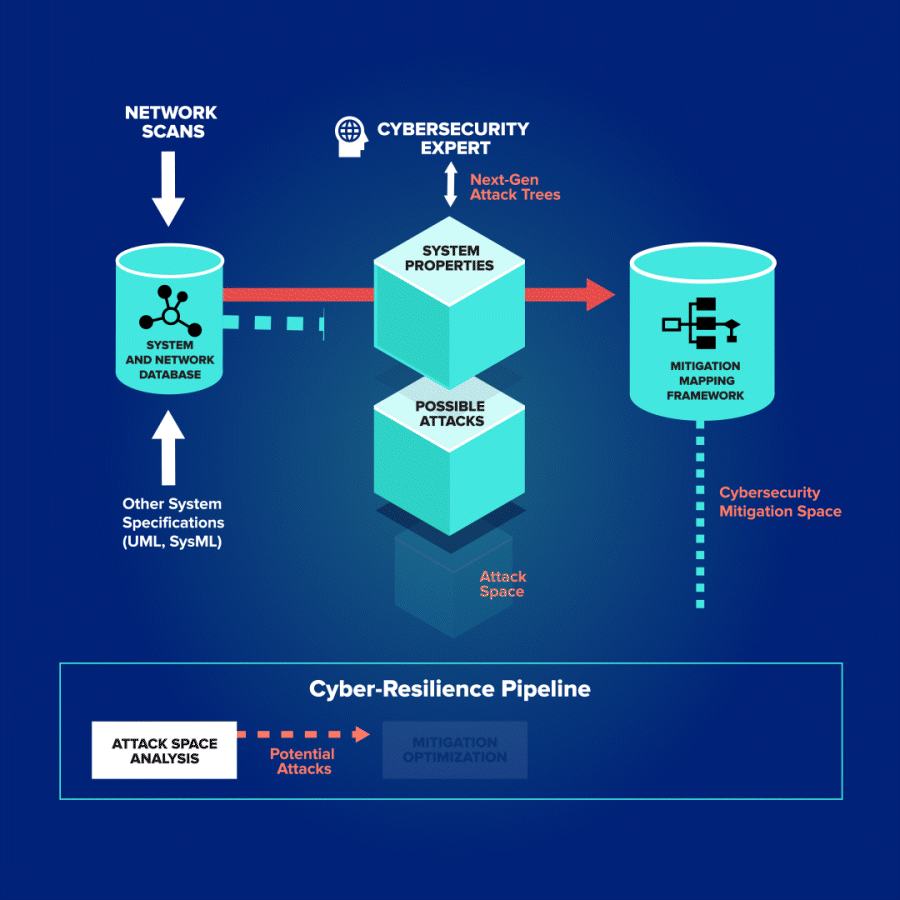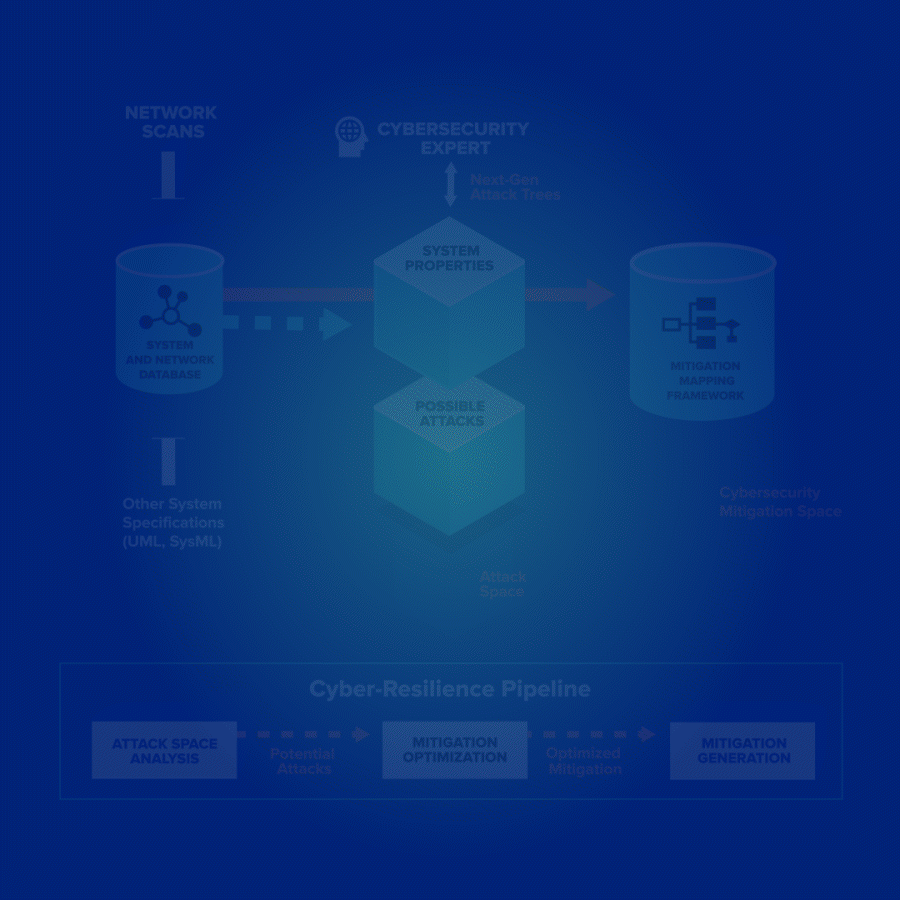
Odineye can scan an entire enterprise—mobile, web, hosts, and servers—to provide automated risk assessments and mitigation plans that are prioritized based on impact and lead to tangible cost savings.



Key Features
Mitigation Optimization
Odineye analyzes the attack surface and determines the costs and risks associated with each vulnerability to ensure you address high-priority vulnerabilities first. Security teams are no longer overwhelmed by thousands of potential system vulnerabilities; you can effectively allocate limited security resources.


Odineye delivers the cyber resilience you need
Vulnerabilities and associated risks tied to individual system components
Prioritized list of cost-effective mitigations to increase cyber resiliency
Risk and cost optimization graphs
Mapping of individual mitigations to the attacks they protect against
Precise quantification of possible attacks and associated risks
Prioritization of response based on threat type

License Odineye
System requirements
- Windows® 7, Windows® 10 operating system
- Intel® Atom E3845 or better
- Java 8 or newer

