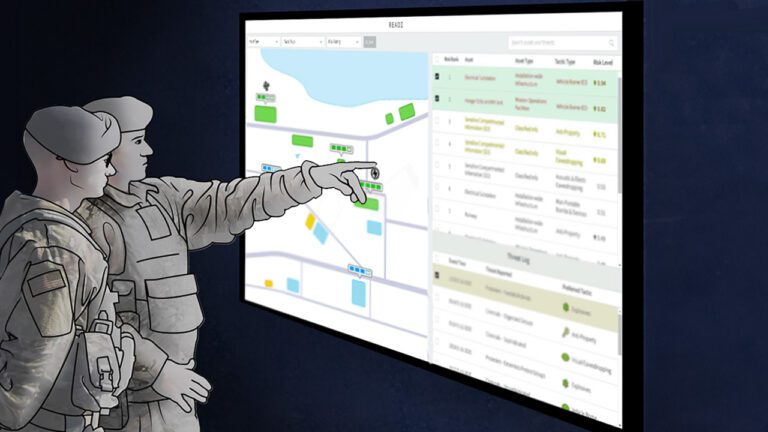
CYBERSECURITY
Developing tested offensive and defensive strategies to win the cyber war
Charles River Analytics delivers comprehensive novel and intelligent solutions for cybersecurity. Our solutions address resilience, mitigation, and data handling, all while decreasing the load on cyber analysts. Our team of interdisciplinary experts brings innovative approaches to known problems in the industry. These solutions are as varied as the breadth of our core IP—from finding existing security breaches by applying our AI algorithms to identifying and eliminating vulnerabilities from the start. Cybersecurity software products from Charles River help both government agencies and private enterprises tackle their most complex cybersecurity challenges.
Leading-Edge R&D
Our talent bench comprises the brightest minds in technology trained in the latest in advanced disciplines like machine learning, deep neural networks, and cognitive science. We work on the leading-edge of cybersecurity research and deliver powerful solutions tailored for today’s systems.
Holistic
Cybersecurity is about playing both offense and defense strategically. Our tools are designed to address problems in a holistic fashion and are made for all the ways in which agencies and enterprises use data. Protecting data in flight and detecting and mitigating cyberattacks in real time are just two of the many ways in which software from Charles River Analytics addresses the challenges posed in today’s cyber warfare.
Innovation
Cybersecurity is a rapidly evolving field and analysts cannot afford to rest on tired strategies. Our experts use advances in adjacent technologies such as computational linguistics and AI to analyze new challenges with fresh insights and innovative approaches.
Automation
We understand the strains on cybersecurity talent, so our tools augment analyst skills so they can work strategically. Automation addresses the rote tasks of cybersecurity, liberating analysts from drudgery and enabling them to solve the larger puzzle.
Cyber Risk and Vulnerability Analysis
Vulnerabilities can sneak into cyber systems through the design and coding of software and firmware in devices. We use robust methods, many of them techniques borrowed from computational linguistics and repurposed for analyzing cyber systems, to detect vulnerabilities, analyze their risk potential, and suggest fixes as necessary.
Malware Analysis and Detection
Malware attacks are increasing in frequency, especially as the number of intrusion points increases. Our experts develop multipronged strategies to address the problem. Our software prevents malware attacks and can predict how the malware will evolve for more efficient mitigation if an attack should occur. Charles River develops systems to keep the warfighter safe from malware intrusions on the ground, in the air, and at sea.
Real-Time Cyberattack Detection and Mitigation
A robust prevention technique is an essential component of cybersecurity strategy. Detecting and mitigating the effect of cyberattacks, if and when they do happen, is equally important. Our sophisticated suite of tools scans IT systems and hardware devices during run time to detect malicious activity. Our software applies advanced anomaly detection and behavior recognition techniques based on parsing techniques adopted from computational linguistics to analyze attacks. Tools from Charles River are skilled at describing the attack and suggesting remediation techniques for ones that are truly malicious.

CyGRAMMAR
Parse and prioritize system alerts in avionic systems and mitigate in-flight attacks in real time.
CyLearn
Detect and infer cyberattacks.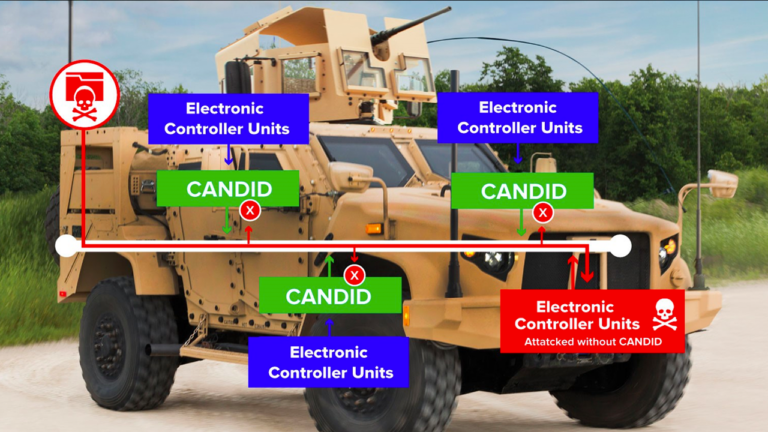
CANDID
Detect, mitigate, and prevent cybersecurity attacks on military ground vehicles.
SLICK
Automatically verify code, catch errors, and seamlessly make recommendations.Resilience and Networking
Automating the tasks of securing systems when legitimate threats are detected keeps mission-critical systems functioning as they should. Such techniques also lower routine maintenance costs. We understand that robust cybersecurity is not limited to IT departments alone but to operating systems as well. Our software keeps all kinds of networks cyber resilient and does the job with existing components.
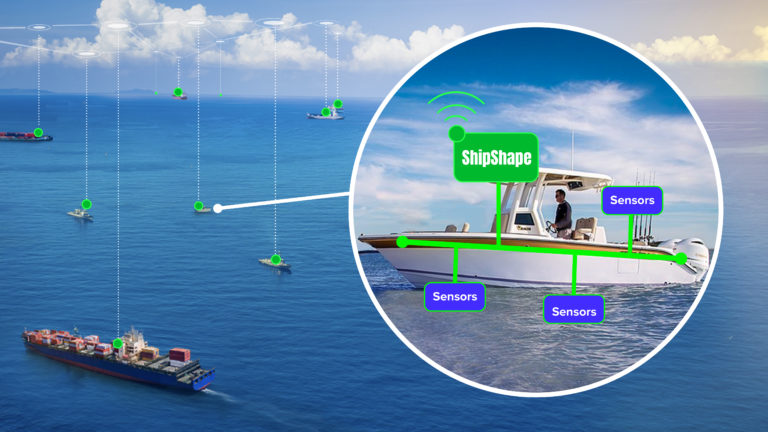
ShipShape
Get boat safety alerts and sensor performance data connected to a vast network.
CyGRAMMAR
Parse and prioritize system alerts in avionic systems and mitigate in-flight attacks in real time.
PRINCESS
Enable autonomous adaptation of software to changes in its environment.
SPNN
Securely train deep neural networks using privacy-prevention encryption.Training and Adversary Modeling
The cost and frequency of cyberattacks reinforces the need to accurately understand and predict adversary behavior. Advanced technology tools from Charles River complement analysts’ existing strategies and automate resource-intensive tasks so enterprises can proactively harden their security systems. Our software also supports analysts by simulating realistic adversary behavior for training applications.

CADE
Use forensic analysis tools to prevent cyber-technical and cyber-social attacks.
CYMOD
Perform cyber-war-gaming exercises to predict potential attack vectors and proactively prepare .
MOC-WAR
Conduct war-gaming exercises without need for extensive adversary behavior modeling experience.